
Learn how to effortlessly deploy and manage a LAMP stack on RHEL9 using Ansible. Streamline your server setup with automation! Table of Contents Introduction Hey

Learn how to set up and configure Ansible for DevOps automation with our step-by-step guide. Improve your workflow and productivity with Ansible for efficient infrastructure management.
Ansible is an open-source automation tool that simplifies the process of automating configuration management, application deployment, and task execution in DevOps environments. With its straightforward syntax, agentless architecture, and wide community support, Ansible has become one of the leading tools for DevOps automation. Whether you’re managing large-scale infrastructures, deploying applications, or orchestrating complex workflows, Ansible is a versatile solution to streamline these tasks.
This guide will walk you through how to set up and configure Ansible for DevOps automation, starting from the basics and moving towards advanced configurations. By the end of this post, you’ll have a solid understanding of Ansible’s capabilities and how to use it to automate your DevOps workflows.
Before diving into the setup and configuration of Ansible, here are some essential points to keep in mind:
Prerequisites |
Before installing Ansible, ensure your system meets the following prerequisites:
Installation on Ubuntu/Debian-based Systems |
Update your package manager:
sudo apt update -y
sudo apt install ansible -y
ansible --version
This command should output the installed Ansible version.
Installation on Red Hat/CentOS-based Systems |
Install the EPEL repository:
sudo yum install epel-release -y # For CentOS
sudo dnf install https://dl.fedoraproject.org/pub/epel/epel-release-latest-$(rpm -E %rhel).noarch.rpm # For RHEL 8+
sudo yum install ansible -y
sudo dnf install ansible -y # For RHEL 8 or higher
ansible --version
Once Ansible is installed, the next step is to configure it for your specific environment. Ansible uses a configuration file called ansible.cfg to manage settings like SSH parameters, remote user accounts, and module behavior.
Default Configuration File |
Ansible typically looks for ansible.cfg in the following order:
In the current working directory
In your home directory (
~/.ansible.cfg)
In
/etc/ansible/ansible.cfg
If none of these files exist, you can create a new one. Here’s an example of a basic ansible.cfg file:
[defaults]
inventory = ./inventory
remote_user = your_user
host_key_checking = False
This file tells Ansible to use a local inventory file and disables host key checking for SSH (useful for testing but should be enabled in production).
Ansible uses an inventory file to define the machines (hosts) that it will manage. The inventory file can be in either INI or YAML format. Below is an example of an INI-style inventory file.
Example of an INI Inventory File |
[web_servers]
web1.example.com
web2.example.com
[db_servers]
db1.example.com
db2.example.com
You can also create a dynamic inventory file that fetches the list of hosts from an external source like AWS, Azure, or Google Cloud.
Example of a YAML Inventory File |
all:
hosts:
web1.example.com:
ansible_user: your_user
db1.example.com:
ansible_user: your_user
children:
web_servers:
hosts:
web1.example.com
web2.example.com
db_servers:
hosts:
db1.example.com
db2.example.com
Playbooks are Ansible’s configuration, deployment, and orchestration language. They are YAML files that define a series of tasks to be executed on specified hosts.
Example of a Simple Playbook |
---
- name: Install Apache on web servers
hosts: web_servers
become: yes
tasks:
- name: Install Apache
apt:
name: apache2
state: present
- name: Start Apache service
service:
name: apache2
state: started
To run the playbook, use the following command:
ansible-playbook -i inventory playbook.yml
This command will execute the tasks defined in the playbook.yml file on the hosts listed in the inventory file.
Roles in Ansible allow you to group tasks, variables, files, templates, and handlers into reusable components. Using roles improves organization, readability, and modularity of your playbooks.
Example of Role Directory Structure |
roles/
├── apache
│ ├── tasks/
│ │ └── main.yml
│ ├── handlers/
│ │ └── main.yml
│ ├── defaults/
│ │ └── main.yml
To use the apache role in your playbook:
---
- name: Configure Apache
hosts: web_servers
become: yes
roles:
- apache
Roles allow you to create reusable automation components that can be shared across multiple playbooks.
When using Ansible for DevOps automation, there are several best practices to ensure that your automation process is efficient, maintainable, and scalable.
1. Use Version Control for Playbooks |
Keep your playbooks in version control (e.g., Git) to track changes, collaborate with teams, and easily roll back changes if needed.
2. Use Variables and Templates |
Make your playbooks more dynamic by using variables for configuration options. You can define variables in the playbook or in separate files. Here’s an example of a variable usage in a playbook:
- name: Install Apache on web servers
hosts: web_servers
vars:
apache_package: apache2
tasks:
- name: Install Apache
apt:
name: "{{ apache_package }}"
state: present
3. Group Hosts in the Inventory |
Use host groups in your inventory file to manage different sets of servers (e.g., web servers, database servers) separately.
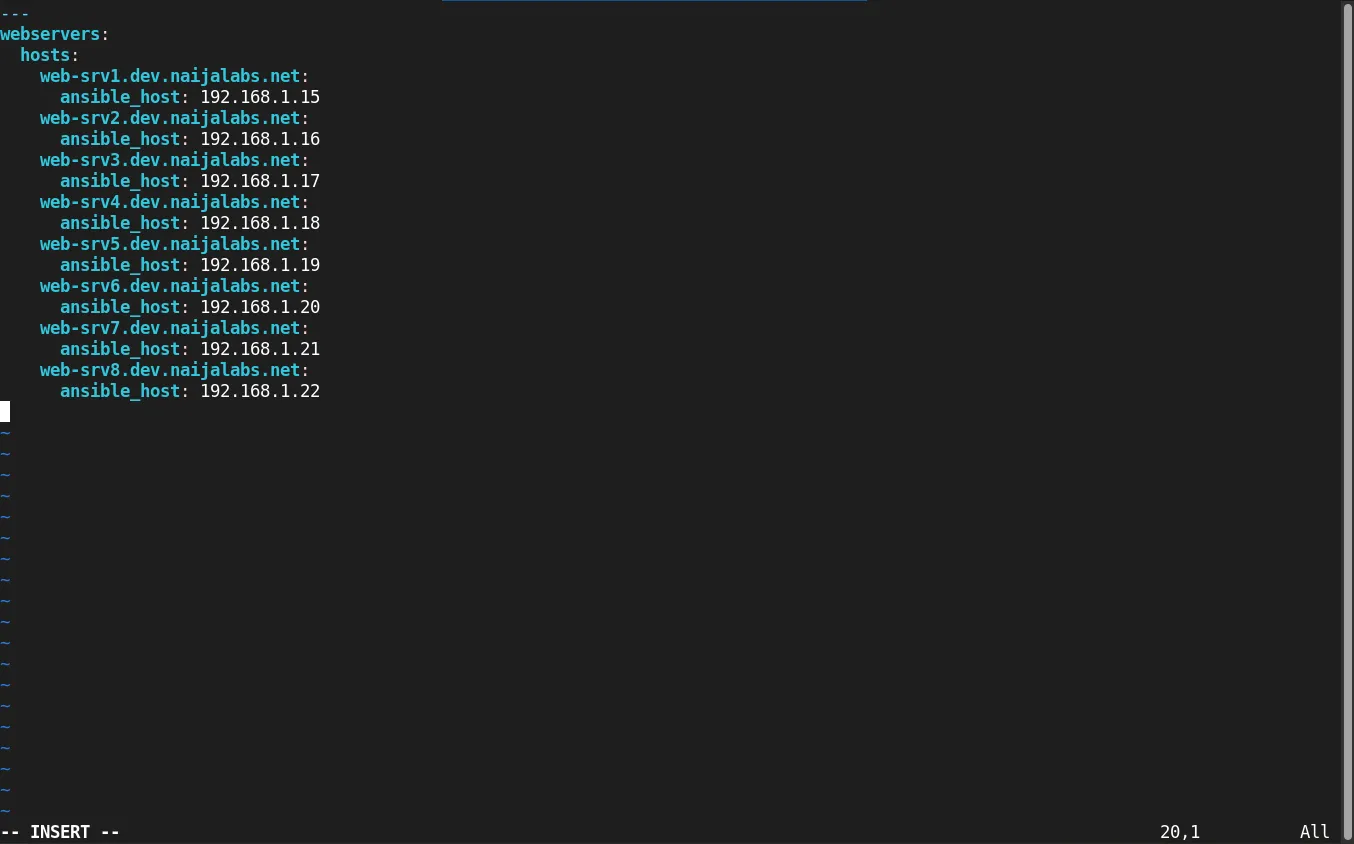
Photo by admingeek from Infotechys
4. Use Ansible Vault for Secrets Management |
Sensitive data such as passwords should never be hardcoded in your playbooks. Instead, use Ansible Vault to encrypt sensitive information.
ansible-vault create secrets.yml
| Step | Action | Command/Example |
|---|---|---|
| Installation | Install Ansible | sudo apt install ansible (Ubuntu) / sudo yum install ansible (CentOS) |
| Configuration File | Create/Edit ansible.cfg | inventory = ./inventory, remote_user = your_user |
| Inventory | Define hosts | INI/YAML format inventory examples as shown above |
| Playbook Example | Create a simple playbook | ansible-playbook -i inventory playbook.yml |
| Roles | Create reusable roles | Directory structure for roles, as shown above |
| Best Practices | Version control, Variables, Vault | ansible-vault create secrets.yml |
Ansible is a powerful tool for automating repetitive tasks in DevOps environments. By following the steps outlined in this guide, you can set up and configure Ansible to automate your infrastructure, deployments, and more. With proper use of playbooks, roles, and inventory files, Ansible can significantly improve your workflow efficiency and reduce errors caused by manual intervention.
By adhering to best practices, such as using version control, Ansible Vault, and organizing tasks using roles, you’ll ensure that your automation is scalable, secure, and easy to maintain.
Did you find this article useful? Your feedback is invaluable to us! Please feel free to share this post and your thoughts in the comments section below.

Learn how to effortlessly deploy and manage a LAMP stack on RHEL9 using Ansible. Streamline your server setup with automation! Table of Contents Introduction Hey

Learn how to install Ansible Tower on RHEL 9 with this comprehensive step-by-step guide. Covering prerequisites, system requirements, and post-installation tasks, this resource is perfect for

Learn how to install Kubernetes using Ansible on Ubuntu 24.04. This comprehensive guide covers prerequisites, setup, and configuration, ensuring a streamlined and consistent deployment process.
