
In this article, we will explore how to use SSH tunneling on Linux, as well as, go over some SSH tunneling examples to demonstrate its

Discover the best practices for securing SSH connections on Linux servers. Learn essential security tips like disabling root login, using SSH keys, and more for better protection and control over your server.
Secure Shell (SSH) is a widely used protocol for remote administration and file transfer on Linux servers. However, due to its popularity, SSH is often a target for malicious actors looking to gain unauthorized access to your server. Securing SSH connections is crucial for maintaining server integrity, confidentiality, and availability. In this post, we’ll explore the best practices for securing SSH connections on Linux servers, with practical examples and explanations.
By following these tips, you can significantly reduce the risk of unauthorized access and ensure that your server remains safe and resilient against attacks.
One of the simplest yet most effective ways to secure your SSH connections is by using SSH key pairs rather than passwords. SSH keys provide a higher level of security because they are difficult to brute-force compared to traditional passwords.
Why SSH Keys are More Secure |
How to Set Up SSH Key Authentication |
ssh-keygen -t rsa -b 4096
Follow the prompts to save the key and optionally add a passphrase for extra security.
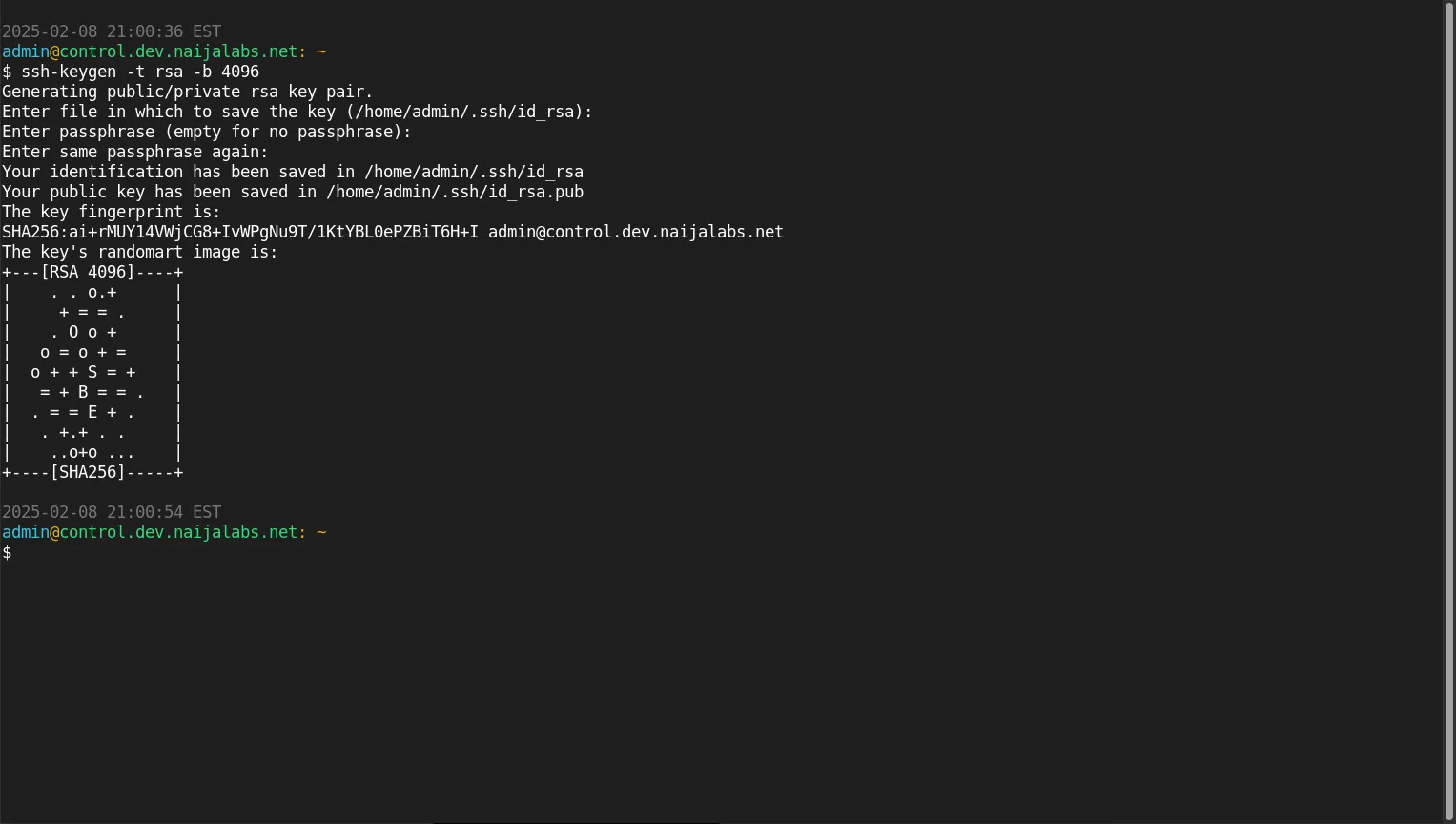
Photo by admingeek from Infotechys
ssh-copy-id user@server_ip
sudo vim /etc/ssh/sshd_config
Find the line:
PasswordAuthentication yes
And change it to:
PasswordAuthentication no
Finally, restart SSH to apply the changes:
sudo systemctl restart sshd
Allowing direct root login over SSH is a security risk. If an attacker gains access to your SSH key or password, they would have complete control over the server. Therefore, it’s recommended to disable root login.
How to Disable Root Login |
sudo vim /etc/ssh/sshd_config
Find the line:
PermitRootLogin yes
And change it to:
PermitRootLogin no
sudo systemctl restart sshd
By disabling root login, users will need to log in with a regular user account first, and then escalate privileges using sudo or su.
Adding an additional layer of security with two-factor authentication (2FA) is highly recommended. Even if an attacker manages to compromise your SSH key or password, they would still need the second factor to authenticate successfully.
How to Set Up 2FA for SSH |
sudo apt-get install libpam-google-authenticator
sudo vim /etc/pam.d/sshd
Add the following line at the end:
auth required pam_google_authenticator.so
google-authenticator
Follow the prompts to configure 2FA, then use an app like Google Authenticator or Authy on your phone to scan the provided QR code.
sudo vim /etc/ssh/sshd_config
Set ChallengeResponseAuthentication to yes:
ChallengeResponseAuthentication yes
sudo systemctl restart sshd
Now, when logging in, you’ll be prompted for a code from your 2FA app, adding another layer of security to your SSH connection.
Restricting SSH access to specific IP addresses can reduce the attack surface of your server. Only trusted IP addresses should be allowed to connect via SSH.
How to Limit SSH Access |
sudo nano /etc/ssh/sshd_config
Add the following line to allow only specific IP addresses:
AllowUsers user@trusted_ip
Or you can use the sshd configuration to restrict access based on IP ranges:
AllowUsers user@192.168.1.*
sudo systemctl restart sshd
The default SSH port (22) is well-known and often targeted by attackers. Changing the SSH port to a less common number can help reduce the risk of automated attacks.
How to Change the SSH Port |
Edit the SSH configuration file:
sudo vim /etc/ssh/sshd_config
Look for the line:
Port 22
Change it to another number, such as 2222:
Port 2222
Save the file and restart SSH:
sudo systemctl restart sshd
Update your firewall rules to allow the new port:
sudo ufw allow 2222/tcp && sudo ufw reload # Ubuntu/Debian-based distributions
sudo firewall-cmd --permanent --add-port=2222/tcp && sudo firewall-cmd --reload # RHEL/CentOS/Linux-based distributions
Fail2Ban is a tool that scans log files for suspicious login attempts and blocks IP addresses that exceed the maximum allowed number of failed attempts. This helps prevent brute-force attacks on SSH.
How to Install and Configure Fail2Ban |
sudo apt-get install fail2ban -y
sudo vim /etc/fail2ban/jail.local
Add or modify the section for SSH:
[sshd]
enabled = true
port = ssh
maxretry = 3
bantime = 3600
sudo systemctl restart fail2ban
Fail2Ban will now automatically block IP addresses that exceed the maximum number of failed login attempts, significantly improving SSH security.
Timeouts and session limits are important for preventing unauthorized users from keeping idle sessions open indefinitely. This is especially important for shared environments or multi-user systems.
How to Configure SSH Timeouts |
Set the ClientAliveInterval and ClientAliveCountMax parameters in the SSH configuration to automatically disconnect idle sessions.
sudo vim /etc/ssh/sshd_config
Add or modify the following lines:
ClientAliveInterval 300
ClientAliveCountMax 0
Finally, restart SSH:
sudo systemctl restart sshd
One of the most important steps in maintaining server security is ensuring that your SSH software, system packages, and dependencies are regularly updated. Security patches are often released to address known vulnerabilities.
How to update your system |
sudo apt update -y && sudo apt upgrade -y
sudo yum update -y # For RHEL/CentOS/Linux-based distributions
sudo dnf update -y # For RHEL 8+/CentOS 8+/Linux-based distributions
sudo apt-get install --only-upgrade openssh-server
By keeping your system up to date, you ensure that any security vulnerabilities in SSH or other software are patched promptly.
Securing SSH connections on Linux servers is essential for maintaining a secure and robust environment. By following these best practices—such as using SSH keys, disabling root login, enabling 2FA, and limiting access by IP—you can significantly enhance the security of your SSH connections. Combining these practices with regular updates and monitoring tools like Fail2Ban will provide a multi-layered defense against malicious actors.
Always remember, server security is an ongoing process, so keep educating yourself and stay proactive in defending your infrastructure.
Did you find this article useful? Your feedback is invaluable to us! Please feel free to share this post!

In this article, we will explore how to use SSH tunneling on Linux, as well as, go over some SSH tunneling examples to demonstrate its

Learn how to install Cluster SSH on Linux distributions of various flavors including Ubuntu, Debian, CentOS, and Fedora. This comprehensive guide will help system administrators

In this article, we will discuss SSH Weak Key Exchange Algorithms and how we can resolve them to enhance the security of SSH connections and
