
Explore the top 10 must-deploy apps for your Kubernetes cluster, from Jenkins for CI/CD automation to Kafka for real-time data processing, and even a Minecraft

Learn how to configure etcd with SSL/TLS on RHEL 8 or CentOS 8 for secure communication. This step-by-step guide covers everything from generating certificates to setting up a multi-node etcd cluster.
In today’s world of cloud-native architectures and containerized applications, securing your etcd cluster is paramount. Etcd is a distributed key-value store widely used by Kubernetes for storing configuration data, service discovery, and other critical state information. As a key component in your system’s architecture, it’s essential to ensure that the data stored within etcd is encrypted, and access is tightly controlled.
This guide will walk you through configuring etcd with SSL/TLS on RHEL 8 or CentOS 8 to provide secure communication for your etcd cluster. By the end of this post, you’ll be able to configure etcd with proper encryption, ensuring secure client-server communication and data integrity.
Before you begin, ensure you have the following:
|
|
|
|
|
|
|
💡If you do not have a DNS setup, each node should have the following entries in the |
# Etcd Cluster
192.168.1.219 node1.dev.naijalabs.net node1
192.168.1.223 node2.dev.naijalabs.net node2
192.168.1.224 node3.dev.naijalabs.net node3
First, we need to install etcd on your RHEL 8 or CentOS 8 machine. If you haven’t installed it yet, follow the steps below:
Method 1: Enable PostgreSQL Repository |
sudo dnf install -y https://download.postgresql.org/pub/repos/yum/reporpms/EL-8-x86_64/pgdg-redhat-repo-latest.noarch.rpm
Then, enable the pgdg-rhel8-extras repository with the following command:
sudo dnf config-manager --enable pgdg-rhel8-extras
Method 2: Download etcd from Github |
You can also download the latest version of etcd from Github.
Installing etcd |
sudo dnf install etcd
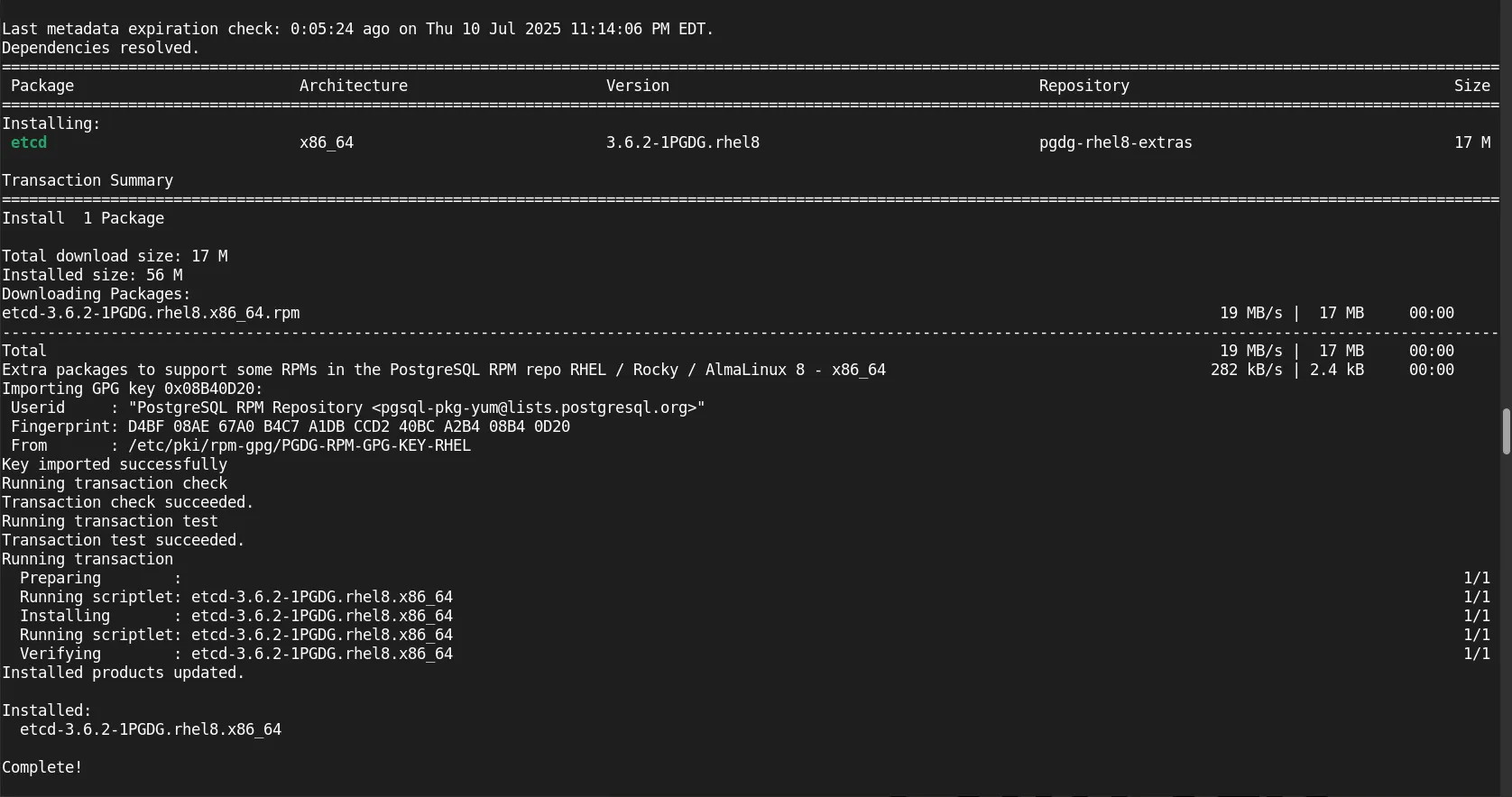
Photo by admingeek from Infotechys
Once installed, verify the etcd service is NOT running:
systemctl status etcd
● etcd.service - Etcd Server
Loaded: loaded (/usr/lib/systemd/system/etcd.service; disabled; vendor preset: disabled)
Active: inactive (dead)
Ensure, the right permissions are set on the /var/lib/etcd directory:
sudo chmod -R 700 /var/lib/etcd
Generating a Self-Signed Certificate |
In this guide, we’ll use OpenSSL to generate a self-signed certificate for securing the etcd communication.
Create a directory for your certificates |
Run the following commands on each node:
mkdir -p /etc/etcd/ssl
cd /etc/etcd/ssl
Generate the server private key and certificate |
openssl genpkey -algorithm RSA -out etcd-server.key -pkeyopt rsa_keygen_bits:2048
openssl req -new -key etcd-server.key -out etcd-server.csr -subj "/CN=etcd-server.local"
openssl x509 -req -in etcd-server.csr -signkey etcd-server.key -out etcd-server.crt -days 365
Generate the client certificate (for secure communication from the client) |
openssl genpkey -algorithm RSA -out etcd-client.key -pkeyopt rsa_keygen_bits:2048
openssl req -new -key etcd-client.key -out etcd-client.csr -subj "/CN=etcd-client.local"
openssl x509 -req -in etcd-client.csr -signkey etcd-client.key -out etcd-client.crt -days 365
Once the certificates are ready, we will configure etcd to use SSL/TLS encryption for both server and client communication.
Edit the etcd configuration file |
On RHEL 8 or CentOS 8, the default etcd configuration file is typically located at /etc/etcd/etcd.conf or /etc/etcd/etcd.conf.yml. If using the default etcd systemd service, you can edit the systemd unit file.
To enable SSL/TLS in etcd, edit the etcd service file (/etc/systemd/system/etcd.service.d/override.conf or /etc/etcd/etcd.conf).
sudo vim /etc/etcd/etcd.conf
Add the following options under the [etcd] section:
ETCD_LISTEN_PEER_URLS=https://0.0.0.0:2380
ETCD_LISTEN_CLIENT_URLS=https://0.0.0.0:2379
ETCD_ADVERTISE_CLIENT_URLS=https://<your-server-ip>:2379
ETCD_CERT_FILE=/etc/etcd/ssl/etcd-server.crt
ETCD_KEY_FILE=/etc/etcd/ssl/etcd-server.key
ETCD_TRUSTED_CA_FILE=/etc/etcd/ssl/ca.crt
ETCD_CLIENT_CERT_AUTH=true
ETCD_PEER_CERT_FILE=/etc/etcd/ssl/etcd-server.crt
ETCD_PEER_KEY_FILE=/etc/etcd/ssl/etcd-server.key
ETCD_PEER_TRUSTED_CA_FILE=/etc/etcd/ssl/ca.crt
Restart the etcd service |
Once you’ve configured the etcd service to use SSL/TLS certificates, restart the etcd service for the changes to take effect:
sudo systemctl daemon-reload
sudo systemctl restart etcd
You can verify that etcd is running and listening on the SSL/TLS-enabled ports:
netstat -tuln | grep 2379
This should show that etcd is listening on https://0.0.0.0:2379 (for client communication) and https://0.0.0.0:2380 (for peer communication).
Now that etcd is secured, let’s test the SSL/TLS configuration using etcdctl with client certificates.
Set the client certificates as environment variables |
export ETCDCTL_API=3
export ETCDCTL_CERT_FILE=/etc/etcd/ssl/etcd-client.crt
export ETCDCTL_KEY_FILE=/etc/etcd/ssl/etcd-client.key
export ETCDCTL_CA_FILE=/etc/etcd/ssl/ca.crt
Try to get a key-value pair from the etcd server |
etcdctl --endpoints=https://<your-server-ip>:2379 get /foo
If everything is set up correctly, you should be able to see the key-value pairs stored in your etcd server.
For a multi-node etcd cluster, repeat the SSL/TLS configuration process on each node. Each node will need to have its own server certificates (or the same certificate if preferred) and peer communication secured using the same TLS configuration.
Try to get a key-value pair from the etcd server |
On all the etcd nodes, ensure that the ETCD_LISTEN_PEER_URLS and ETCD_PEER_* variables are configured to use SSL/TLS:
ETCD_LISTEN_PEER_URLS=https://<node1-ip>:2380,<node2-ip>:2380
ETCD_PEER_CERT_FILE=/etc/etcd/ssl/etcd-server.crt
ETCD_PEER_KEY_FILE=/etc/etcd/ssl/etcd-server.key
ETCD_PEER_TRUSTED_CA_FILE=/etc/etcd/ssl/ca.crt
Restart each node after making changes:
sudo systemctl restart etcd
Securing your etcd cluster with SSL/TLS encryption on RHEL 8 / CentOS 8 is essential to protect the integrity and confidentiality of your critical data. By following this step-by-step guide, you’ve successfully configured SSL/TLS for both server-client and peer-to-peer communications in etcd.
By using secure certificates, encryption, and proper client-server authentication, you ensure that your etcd cluster is resilient against eavesdropping and man-in-the-middle attacks.
Did you find this article helpful? Your feedback is invaluable to us! Feel free to share this post with those who may benefit, and let us know your thoughts in the comments section below.

Explore the top 10 must-deploy apps for your Kubernetes cluster, from Jenkins for CI/CD automation to Kafka for real-time data processing, and even a Minecraft

Learn how to deploy a highly available PostgreSQL cluster on AlmaLinux 9 using Patroni for automatic failover, seamless scaling, and enhanced reliability. Table of Contents

Learn how to install a Kubernetes cluster on RHEL 9 | CentOS 9. Explore step-by-step instructions, best practices, and considerations for smooth deployment and operation.
