
Learn about installing and using PostgreSQL on CentOS 8 with this step-by-step guide and take your data management to the next level! Table of Contents

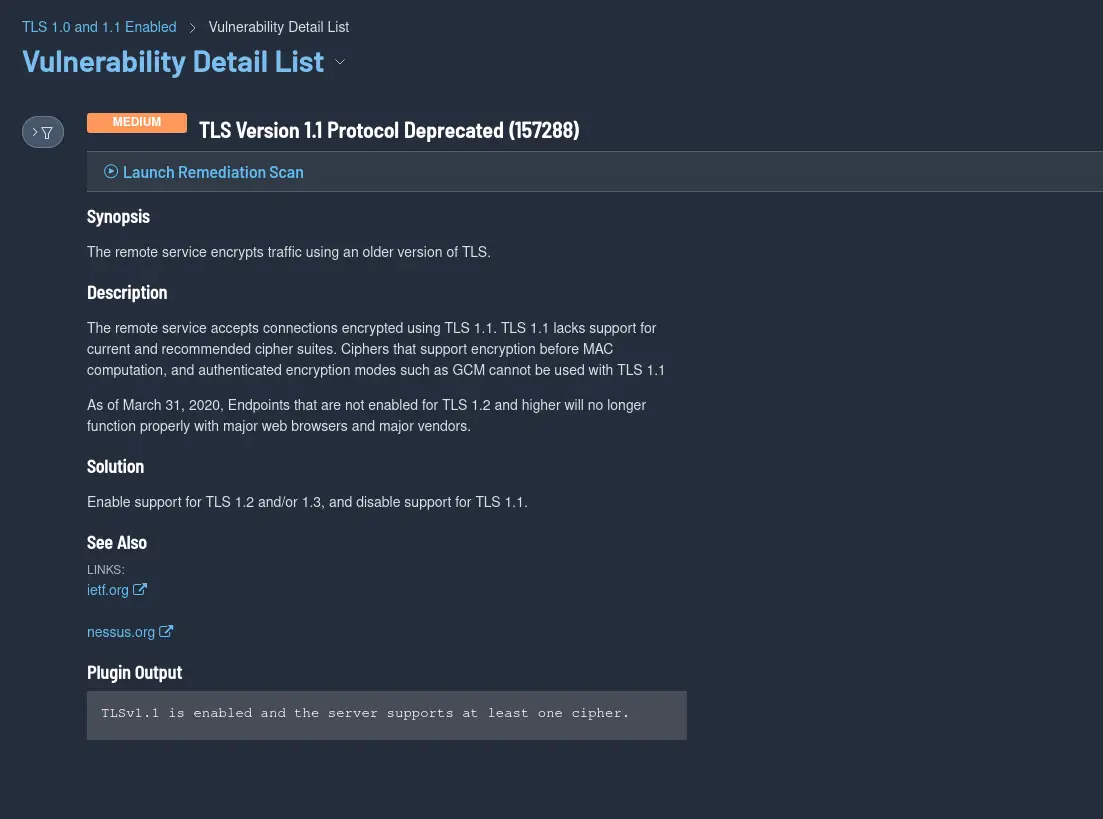
Your security team has just informed you that TLS Version 1.1 Protocol Deprecated (157288) was found on your cockpit server on port 9090. What do you do? In this article, we will explore how to mitigate this Tenable finding.
In today’s world, securing our online communication and protecting sensitive information has become a necessity. One of the most critical components of securing communication is Transport Layer Security (TLS), which is the successor to the Secure Sockets Layer (SSL) protocol. In this article, we will discuss how to enable TLS1.2 on a RHEL7/CentOS7 Cockpit server.
SSL was initially developed by Netscape in the mid-1990s as a way to secure online transactions. However, it was eventually found to have several vulnerabilities, leading to the development of TLS as its successor. The latest version of TLS is TLS1.3, but we will focus on enabling TLS1.2 in this article.
SSL/TLS is a protocol used for encrypting and securing data communication over the internet. It provides a secure channel between two communicating endpoints, ensuring that the data exchanged between them is confidential and tamper-proof.
Secure Renegotiation is a feature in TLS that allows two parties to renegotiate the encryption keys without revealing the plain-text data being transmitted. This feature is designed to prevent attackers from intercepting and tampering with the data being exchanged during the renegotiation process.
This finding indicates that a remote service on your machine is accepting connections encrypted using TLS1.1.
Before we can enable TLS1.2, we need to make sure that OpenSSL is installed on our server. To do this, we can run the following command:
$ sudo yum install openssl -y
Next, create the /etc/systemd/system/cockpit.service.d directory with the following command:
$ sudo mkdir -p /etc/systemd/system/cockpit.service.d
Using your favorite text editor or vim, open a file called ssl.conf under the /etc/systemd/system/cockpit.service.d directory.
$ sudo vim /etc/systemd/system/cockpit.service.d/ssl.conf
Copy and paste the following entries to the ssl.conf file. This will ensure that only the TLS1.2 protocol is enabled by eliminating all the others version.
[Service]
Environment=G_TLS_GNUTLS_PRIORITY=SECURE128:-VERS-SSL3.0:-VERS-TLS1.0:-VERS-TLS1.1
[Service]: This is a section header in a systemd unit file that defines a new service or modifies an existing one.
Environment: This option sets environment variables for the service.
G_TLS_GNUTLS_PRIORITY: This is an environment variable that sets the priority list of SSL/TLS protocols and ciphersuites used by the GnuTLS library.
SECURE128:-VERS-SSL3.0:-VERS-TLS1.0:-VERS-TLS1.1: This is the value of the G_TLS_GNUTLS_PRIORITY environment variable. It specifies the SSL/TLS protocol versions to use and their preferred order, as well as any versions to exclude.
SECURE128 specifies that SSL/TLS connections should use only strong ciphersuites that provide at least 128-bit encryption.:-VERS-SSL3.0 specifies that SSLv3.0 should not be used.:-VERS-TLS1.0 specifies that TLS1.0 should not be used.:-VERS-TLS1.1 specifies that TLS1.1 should not be used.Overall, these entries configure the GnuTLS library to use only strong SSL/TLS ciphersuites with at least 128-bit encryption, and to exclude SSLv3.0, TLS1.0, and TLS1.1 from the list of supported protocols. This helps to ensure that your Cockpit server is using TLS version 1.2 and strong ciphersuites.
In order to implement the ssl.conf file, it is essential to execute a daemon-reload and restart the cockpit service.
$ sudo systemctl daemon-reload; sudo systemctl restart cockpit
After enabling TLS1.2 on your RHEL7/CentOS7 Cockpit server and updating the configuration file, you need to verify that the new protocol is indeed being used.
To verify that TLS1.2 is enabled and in use, you can use the OpenSSL tool by running the following command:
$ openssl s_client -connect localhost:9090 -tls1_2
This command initiates a TLS1.2 connection to your Cockpit server on port 9090 and displays detailed information about the SSL/TLS certificate and the connection parameters.
Additionally, you can also verify the SSL/TLS version used in your web browser when accessing the Cockpit web interface. Simply click on the padlock icon in the browser’s address bar, and you should see the version of SSL/TLS used for the connection.
By verifying that TLS1.2 is enabled and in use, you can ensure that your Cockpit server is using a secure version of the TLS protocol. Finally, launch a remediation scan in Tenable and confirm the finding has been mitigated.
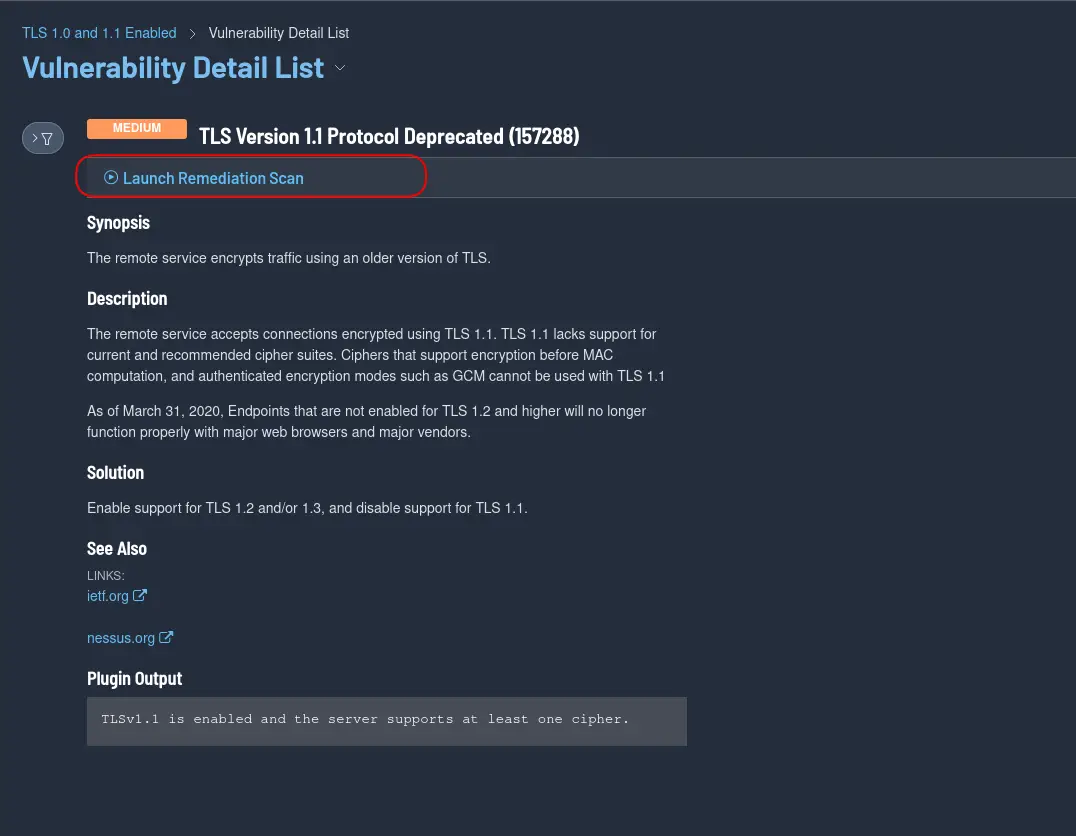
Congratulations! You have successfully enabled TLS1.2 on your RHEL7/CentOS7 Cockpit server.
We have reviewed how to enable TLS1.2 on a RHEL7/CentOS7 Cockpit server. By following the steps outlined in this article, you can ensure that your server is using the latest and most secure version of the TLS protocol, providing a secure channel for your online communication.
Remember to keep your SSL/TLS certificate up-to-date and verify its validity to ensure that it’s trusted by your clients. Was this article helpful to you? If so, leave us a comment below and share!
Related Posts

Learn about installing and using PostgreSQL on CentOS 8 with this step-by-step guide and take your data management to the next level! Table of Contents

Are you looking to secure your Cockpit server and protect sensitive data? Follow these steps to Install SSL Certificates on Cockpit and protect your server

In this article, we will examine installing and using Gitlab on Ubuntu server version 20.04. Gitlab community edition or Gitlab CE can be installed by
