Install Remmina on RHEL9 or CentOS9

In this guide, we’ll walk you through the step-by-step process of installing Remmina on RHEL9 or CentOS9. Remmina is a feature-rich remote desktop client that allows you to connect to various remote desktop protocols such as RDP, VNC, SSH, and more, all from a single application. Table of Contents 🚀 Introduction Remmina, an open-source remote desktop […]
Setting Up a CI/CD Pipeline with Jenkins on RHEL9: A Step-by-Step Guide

In this article, we explore the seamless integration of CI/CD with Jenkins on RHEL9, providing a detailed step-by-step guide for setting up an efficient and automated development pipeline. Table of Contents Introduction In the fast-paced world of software development, Continuous Integration (CI) and Continuous Delivery (CD) have become essential practices for ensuring the reliability and […]
Install MySQL on RHEL9 or CentOS9
Are you looking to set up MySQL on your RHEL 9 or CentOS 9 server? Follow these detailed steps to install MySQL on RHEL 9 or CentOS 9. Table of Contents Introduction Whether you’re a seasoned system administrator or a newcomer to database management, this step-by-step guide will walk you through the process of installing MySQL on […]
Btrfs or LVM: Which is a better filesystem?

In this article, we will compare Btrfs and LVM and determine which filesystem is better. This should be an interesting read…why you ask? Table of Contents Introduction Well, depending on how long you’ve been a sysadmin or a Linux enthusiast, you may have never heard of Btrfs. However, many IT professionals have a good grasp […]
Install RHEL9 on KVM

In this tutorial, we’ll guide you through the step-by-step installation of RHEL9 on KVM. The process is uncomplicated, and we’ll present it in a format similar to the one used in the “Install CentOS8 on KVM” article. Table of Contents Introduction Please be aware that we will be installing RHEL9 on a qcow2 formatted disk, providing […]
Install Squid Proxy on RHEL9 or CentOS9

In this guide, we will walk you through the step-by-step installation of Squid Proxy on RHEL9 or CentOS9, catering to the needs of IT professionals seeking a robust and reliable solution for managing internet traffic. Table of Contents Introduction In the ever-evolving landscape of IT infrastructure, the need for efficient and secure internet access has […]
Add a Virtual Bridge Using NMCLI
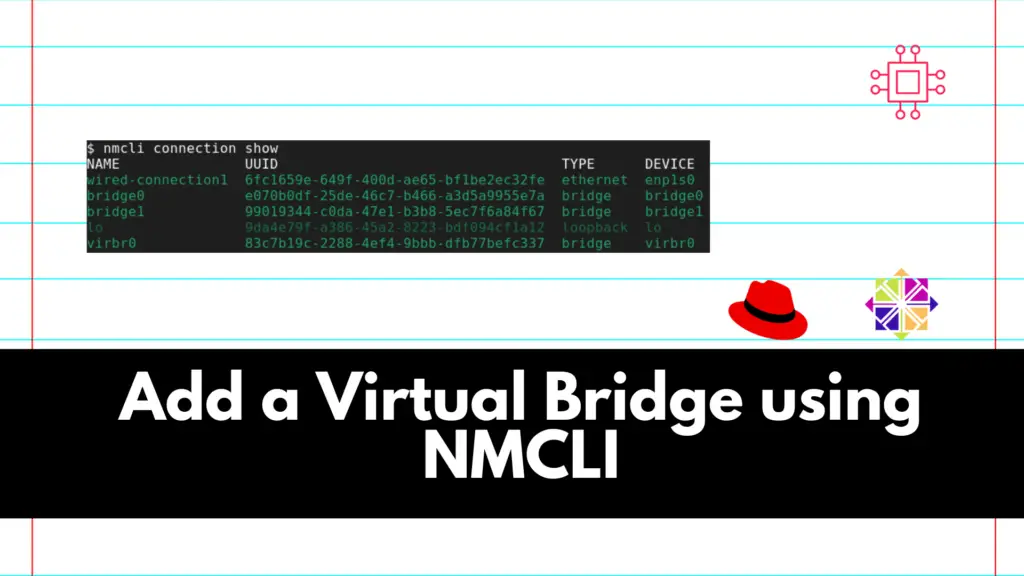
Adding a virtual bridge using nmcli involves several steps. A virtual bridge is commonly used in networking to connect multiple virtual or physical network interfaces. Table of Contents Introduction In networking, a virtual bridge serves as a crucial component for connecting and managing multiple network interfaces. It allows for the creation of a unified network […]
How to calculate pi using a bash script
To calculate pi using a Bash script, you can use the bc command, which is a tool that can perform arithmetic operations in the terminal. Table of Contents Introduction By following our step-by-step guide, you’ll learn how to calculate pi using a Bash script while gaining a thorough understanding of the underlying code. We’ll review […]
Creating MBR partitions in Linux

In this article, we’ll learn about creating MBR partitions in Linux, delve into the procedure using the fdisk and parted tool, and provide clear command line examples to illustrate its utility. Table of Contents Introduction Efficiently managing storage is a critical aspect of IT infrastructure. Whether you’re setting up servers, workstations, or virtual machines, understanding […]
Install KeepassXC on RHEL9 or CentOS9

Learn how to successfully install KeePassXC on RHEL 9 or CentOS 9 for efficient password management and security. Table of Contents Introduction KeePassXC is a popular open-source password manager that offers secure storage for sensitive information. Developed as a community-driven fork of KeePassX, it is designed to work seamlessly on multiple operating systems, including Linux. […]
