
Learn how to implement full disk encryption on RHEL 9 or CentOS 9 for Zabbix running PostgreSQL database. This step-by-step guide helps secure your monitoring server
A complete guide to enterprise network infrastructure—covering DMZ, firewalls, core networks, and hybrid cloud integration. Includes best practices, CLI examples, and design tables for IT professionals.
In today’s digital enterprise, the network infrastructure is the foundation that supports communication, application delivery, and cybersecurity. As organizations scale and hybridize their environments, a well-architected network must ensure security, scalability, and operational efficiency.
This guide breaks down a typical enterprise network infrastructure from the outside (internet edge) to the inside (core and endpoint layers)—illustrating best practices, common components, and design considerations for modern IT environments.
An enterprise network isn’t a single entity—it’s a layered ecosystem. Each layer serves a unique purpose and communicates through well-defined interfaces.
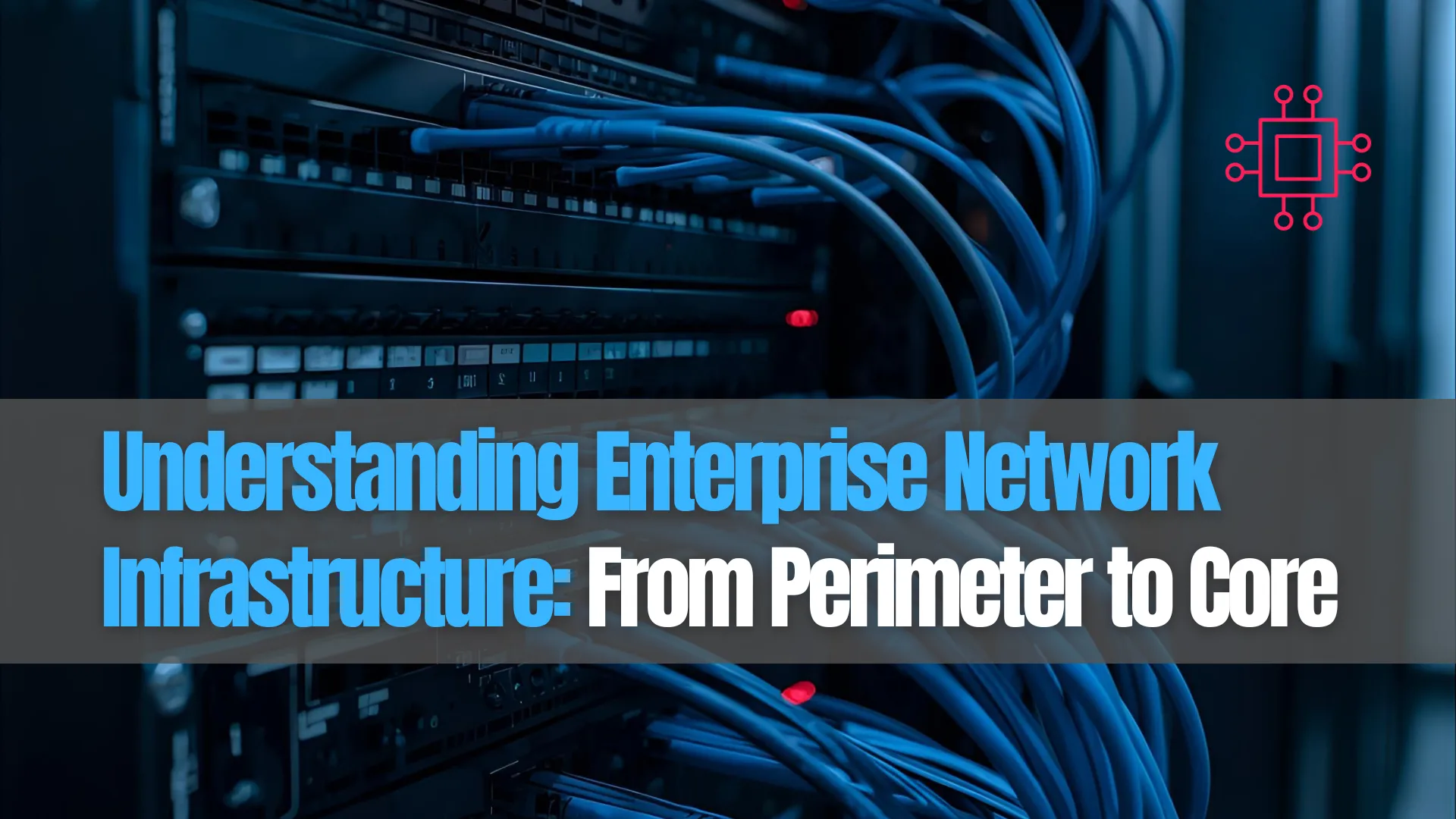
The diagram below (as generated earlier) illustrates the flow of network connectivity:
| Layer | Core Components | Primary Function | Example Devices |
|---|---|---|---|
| Internet / WAN | ISP links, Cloud peers | External connectivity | Internet routers, SD-WAN edges |
| Perimeter Layer | Firewalls, DMZ, IDS/IPS | Traffic inspection and threat prevention | Palo Alto, Fortinet, Check Point |
| Edge / Distribution | Core switches, routers | Aggregation and routing | Cisco Catalyst, Juniper MX |
| Internal Network | Servers, virtualization nodes | Business application hosting | VMware ESXi, Red Hat, Hyper-V |
| Access Layer | Switches, Wi-Fi APs | User/device connectivity | Aruba, Cisco Meraki, Ubiquiti |
This tiered model ensures redundancy, performance optimization, and isolation of critical assets.
🟢 Connectivity Types |
Enterprises connect to the outside world through various high-availability and redundant links such as:
|
|
|
|
🟢 Example: Checking WAN Interface Status |
A common command-line check for a Cisco or Linux edge router:
# For Linux
ip -s link show eth0
# For Cisco IOS
show interfaces GigabitEthernet0/1
Ensuring uptime at this layer is critical—any failure here cascades to all downstream systems.
The perimeter network, often called the DMZ (Demilitarized Zone), acts as a controlled buffer between the untrusted internet and internal assets. It typically contains:
|
|
|
|
🟢 CLI Example: Viewing Firewall Rules |
# Linux example (iptables)
sudo iptables -L -v
# Palo Alto PAN-OS (CLI)
show running security-policy
| Control | Purpose | Implementation Tip |
|---|---|---|
| Firewall Policy Segmentation | Limits east-west exposure | Use zones for DMZ, LAN, and WAN |
| IDS/IPS Integration | Detects malicious payloads | Mirror traffic via SPAN port |
| Geo-blocking | Reduces unwanted access | Filter non-business regions |
| TLS Termination | Offload SSL inspection | Use reverse proxy or dedicated device |
Strong perimeter design sets the tone for zero-trust enforcement deeper in the network.
The edge/distribution layer links perimeter and internal zones. It’s responsible for routing, traffic segmentation, and policy enforcement.
Typical components:
|
|
|
|
🟢 Key Configuration Example |
# Cisco IOS VLAN setup
interface GigabitEthernet0/2
description HR Network
switchport mode access
switchport access vlan 30
spanning-tree portfast
🟡 Edge Layer Best Practices |
|
|
|
Photo by admingeek from Infotechys
At the center of the enterprise lies the core network—where applications, data, and services reside.
It’s built for speed, reliability, and scalability.
🟢 Core Infrastructure Includes |
|
|
|
|
|
🟢 High Availability Design Example |
| Component | Redundancy Method | Notes |
|---|---|---|
| Core Switches | Dual chassis with MLAG | Active-active data paths |
| Databases | Multi-node replication | Async or synchronous |
| Load Balancers | HA pair | One active, one standby |
| Power / Cooling | Dual circuits | Prevents data center downtime |
💡Pro tip: The core should have 10-40Gbps uplinks to distribution switches to avoid bottlenecks. |
The internal layer connects end-user devices to enterprise resources securely and efficiently.
Typical elements:
|
|
|
|
🟢 CLI Example: Verifying Device Connectivity |
# Check MAC address table on a switch
show mac address-table
# Or on Linux client
ip addr show
ping -c 3 gateway.local
🟡 Access Control Model |
| User Type | Network Segment | Authentication | Typical VLAN |
|---|---|---|---|
| Employees | Corporate LAN | AD + MFA | VLAN 10 |
| Guests | Isolated Wi-Fi | Captive Portal | VLAN 20 |
| IoT Devices | Restricted Segment | MAC-based | VLAN 30 |
These segmentations form the basis of zero-trust networking—treating every access request as potentially hostile until verified.
Across all layers, enterprises implement centralized monitoring, automation, and identity management tools.
🟢 Common Systems Include |
|
|
|
|
🟢 Example: Monitoring Network Latency via CLI |
ping -c 10 core-switch.domain.com
traceroute db-server.domain.com
🟡 Monitoring Framework Table |
| Category | Tool Example | Function |
|---|---|---|
| Performance | Zabbix, Prometheus | CPU, bandwidth, uptime |
| Security | Splunk, QRadar | Event correlation |
| Automation | Ansible, Terraform | Network provisioning |
| Backup | Veeam, Bacula | Disaster recovery and resilience |
Modern enterprises often extend their data centers into cloud environments to improve scalability and reduce cost.
This hybrid setup connects on-premises and cloud through secure, high-bandwidth links.
🟢 Cloud Integration Options |
|
|
|
🟢 Example: Verifying VPN Tunnel Status |
# Cisco ASA
show vpn-sessiondb l2l
# AWS CLI Example
aws ec2 describe-vpn-connections --region us-east-1
Hybrid environments demand consistent policies across both sides—ensuring security compliance and unified visibility.
| Category | Key Action | Verification Method |
|---|---|---|
| Redundancy | Implement dual power and paths | Verify with failover test |
| Security | Apply zero-trust principles | Conduct regular audits |
| Monitoring | Centralize logs & metrics | SIEM dashboard |
| Performance | Use QoS and caching | Analyze NetFlow data |
| Scalability | Use modular switches | Capacity planning reports |
| Compliance | Enforce IAM and patching | Policy compliance scans |
The traditional perimeter is dissolving as enterprises embrace remote work, mobile endpoints, and cloud-native applications.
Modern designs emphasize Zero Trust Network Architecture (ZTNA)—verifying users, devices, and sessions continuously.
Key takeaways for enterprises moving forward:
|
|
|
A well-structured enterprise network—layered from the internet edge to the internal core—is essential for maintaining operational resilience and cybersecurity. By combining layered defenses, centralized monitoring, and scalable design, organizations can confidently support hybrid workloads, cloud adoption, and zero-trust strategies.
Whether you’re an architect designing new infrastructure or an administrator maintaining existing systems, mastering these layers ensures that your enterprise stays secure, efficient, and future-ready.
Did you find this article helpful? Your feedback is invaluable to us! Feel free to share this post with those who may benefit, and let us know your thoughts in the comments section below.

Learn how to implement full disk encryption on RHEL 9 or CentOS 9 for Zabbix running PostgreSQL database. This step-by-step guide helps secure your monitoring server

Are you concerned about the security of your network? Learn about for network vulnerabilities scanning using NMAP, a powerful tool that can help you identify

In the article, we’ll delve into how to manage network connections using the NMCLI utility, a powerful command-line tool for configuring and controlling NetworkManager, which
