Explore 20 commonly used SPL commands in Splunk, with example queries for stats, timechart, eval, eventstats, streamstats, rex, and more. Boost your Splunk search skills

Learn how to fix the Splunk allowedDomainList security warning in alert_actions.conf. Prevent unauthorized alert emails and protect sensitive data by configuring domain restrictions correctly.
Splunk administrators often encounter a critical security warning:
⚠️ Found an empty value for ‘allowedDomainList’ in the alert_actions.conf configuration file. |
This alert points to a significant security misconfiguration — one that could allow users to send sensitive data outside your organization via email alerts. This article provides a comprehensive guide to understanding, mitigating, and properly configuring the allowedDomainList setting to secure your Splunk instance.
allowedDomainList in Splunk?The allowedDomainList setting in Splunk’s alert_actions.conf file specifies which email domains are allowed to receive alert messages. If not configured, Splunk permits any domain, creating a potential data exfiltration path.
🚨 Why This Matters |
Leaving allowedDomainList empty means:
|
|
|
|
Here’s the actual warning message administrators might see:
Security risk warning: Found an empty value for 'allowedDomainList' in the alert_actions.conf configuration file. If you do not configure this setting, then users can send email alerts with search results to any domain.
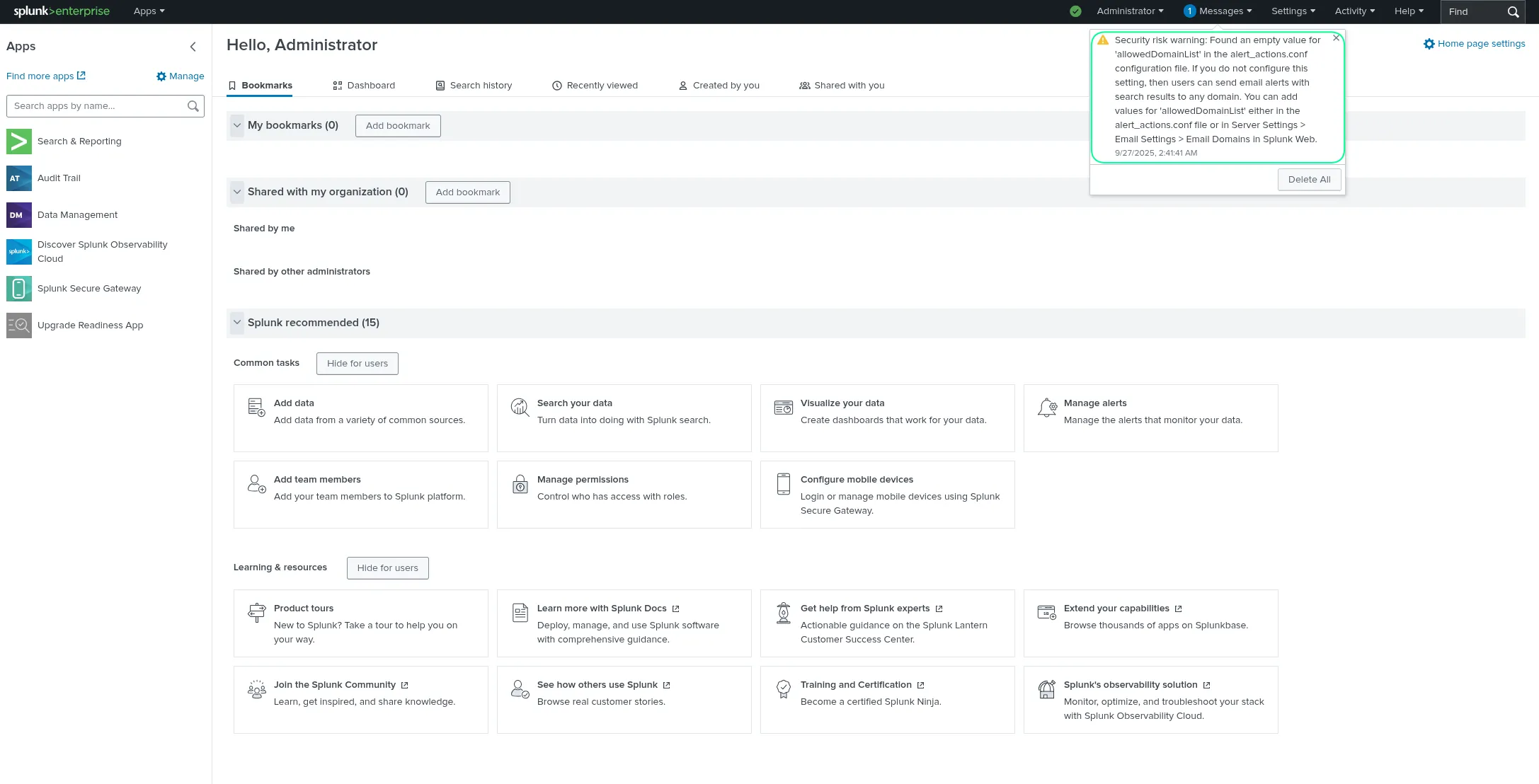
Photo by admingeek from Infotechys
allowedDomainList WarningYou can resolve this misconfiguration in two ways:
🔄 Method 1: Configure in |
First, switch to the root user and define the SPLUNK_HOME environment variable before executing the following commands:
sudo -i
export SPLUNK_HOME=`cat /etc/passwd | grep splunk | awk -F: '{ print $6 }'`
Navigate to your Splunk configuration directory:
cd $SPLUNK_HOME/etc/system/local
Open or create the alert_actions.conf file:
vim alert_actions.conf
Add your organization’s approved email domains:
[email]
allowedDomainList = yourcompany.com, partnercompany.com
Save the file and restart Splunk:
$SPLUNK_HOME/bin/splunk restart
Stopping splunkd...
Shutting down. Please wait, as this may take a few minutes.
.............
Stopping splunk helpers...
Done.
...omitted for brevity...
🔄 Method 2: Configure in Splunk Web UI |
|
|
|
|
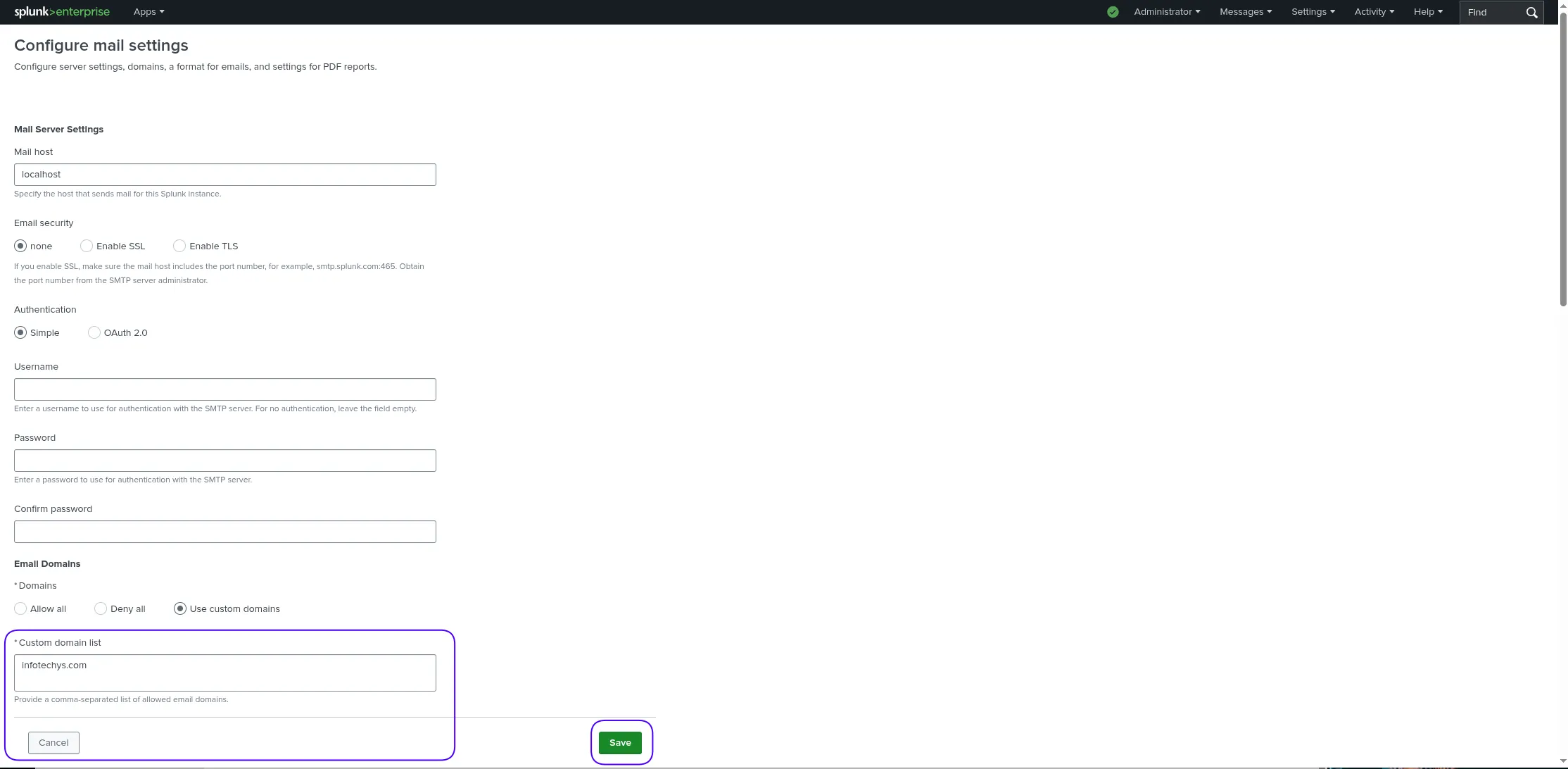
Photo by admingeek from Infotechys
💡NOTE: Splunk Web changes take effect immediately, no restart needed. |
After applying your settings, test the domain restriction:
|
|
Error sending email: Email domain not allowed by 'allowedDomainList'.
| Configuration State | Behavior | Risk Level |
|---|---|---|
allowedDomainList Empty | Users can send alerts to any domain | 🔴 High |
| Configured with Domains | Only specified domains can receive alerts | 🟢 Low |
| Misconfigured (typo, etc.) | Could block legitimate alert delivery or allow leakage | 🟡 Medium–High |
To ensure your Splunk environment remains secure, follow these practices:
▶️ Enforce Domain Restrictions |
Restrict emails to internal and trusted partner domains.
▶️ Use RBAC (Role-Based Access Control) |
Limit who can create or modify alerts. Assign alerting permissions to only trusted roles.
▶️ Log and Audit Alert Actions |
Enable auditing of alert actions. Monitor who sends what alerts to which domains.
▶️ Restrict Free-Text Entry of Email Addresses |
Avoid open input fields where users can enter arbitrary email addresses.
▶️ Update |
In a clustered deployment (SHC), sync this configuration across all search heads.
# Example: Deploy to all search heads using deployment server or Ansible
scp alert_actions.conf user@searchhead1:/opt/splunk/etc/system/local/
scp alert_actions.conf user@searchhead2:/opt/splunk/etc/system/local/
alert_actions.conf Configuration
[email]
mailserver = smtp.yourcompany.com
from = splunk-alerts@yourcompany.com
use_tls = 1
allowedDomainList = yourcompany.com, trustedpartner.com
sendemail = 1
❓ What happens if I leave |
You open up your Splunk instance to unrestricted email alerting, which can result in data exfiltration.
❓ Can I use wildcards in domain names? |
No. allowedDomainList does not support wildcards like *.yourcompany.com. Use specific domains only.
❓ How do I block all external emails? |
Simply include only your internal domains in the list:
allowedDomainList = yourcompany.com
Any email sent outside of yourcompany.com will be blocked.
❓ Does this apply to all Splunk versions? |
Yes, this applies to Splunk Enterprise and Splunk Cloud Platform, although GUI and file locations may vary slightly in managed environments.
| File | Purpose |
|---|---|
alert_actions.conf | Defines alert actions (like email) |
authentication.conf | Sets authentication methods and roles |
authorize.conf | Role-based access control |
outputs.conf | Sets up data forwarding |
If you use an internal SMTP relay (e.g., Microsoft Exchange or Postfix), make sure to:
|
|
smtpd_recipient_restrictions =
check_recipient_access hash:/etc/postfix/allowed_domains
Ignoring the allowedDomainList setting in Splunk can lead to critical data leakage. Fortunately, fixing this security hole is straightforward. Whether through the Splunk Web interface or direct config file edits, setting this parameter ensures that alert emails only go to trusted domains — maintaining your organization’s privacy, compliance, and security posture.
⏱️ Take the time to review your configurations today. A few lines of config can save you from a major incident tomorrow. |
Did you find this article helpful? Your feedback is invaluable to us! Feel free to share this post with those who may benefit, and let us know your thoughts in the comments section below.

Explore 20 commonly used SPL commands in Splunk, with example queries for stats, timechart, eval, eventstats, streamstats, rex, and more. Boost your Splunk search skills

This guide aims to equip you with the knowledge needed to install ELK stack on RHEL9 | CentOS9 effortlessly. By following these steps, you can
Learn how to install Splunk on RHEL9 or CentOS 9 with this beginner-friendly guide. Step-by-step instructions, CLI examples, and troubleshooting tips included. Table of Contents
