
Discover the best practices for securing SSH connections on Linux servers. Learn essential security tips like disabling root login, using SSH keys, and more for

Learn how to manage SELinux contexts on RHEL 9 and CentOS 9 for improved security. This guide covers SELinux contexts, CLI commands, troubleshooting, and best practices.
Security-Enhanced Linux (SELinux) is a crucial security mechanism in Red Hat Enterprise Linux (RHEL) 9 and CentOS 9. It enforces mandatory access control (MAC) policies, preventing unauthorized access to system resources. Understanding SELinux contexts is essential for managing and securing Linux environments effectively.
In this guide, we will explore SELinux contexts, how they impact system security, and how to manage them using CLI commands. This comprehensive tutorial is aimed at improving your knowledge and optimizing security on RHEL 9 and CentOS 9.
What is SELinux? |
SELinux provides an additional layer of security through policy-based access control, enforcing rules on files, processes, and network resources. By default, SELinux is enabled in RHEL 9 and CentOS 9, ensuring a more secure operating environment.
SELinux Modes |
SELinux operates in three modes:
|
|
|
Check the current SELinux mode:
sestatus
SELinux status: enabled
SELinuxfs mount: /sys/fs/selinux
SELinux root directory: /etc/selinux
Loaded policy name: targeted
Current mode: enforcing
Mode from config file: enforcing
Policy MLS status: enabled
Policy deny_unknown status: allowed
Memory protection checking: actual (secure)
Max kernel policy version: 33
To switch modes, edit the configuration file:
sudo vim /etc/selinux/config
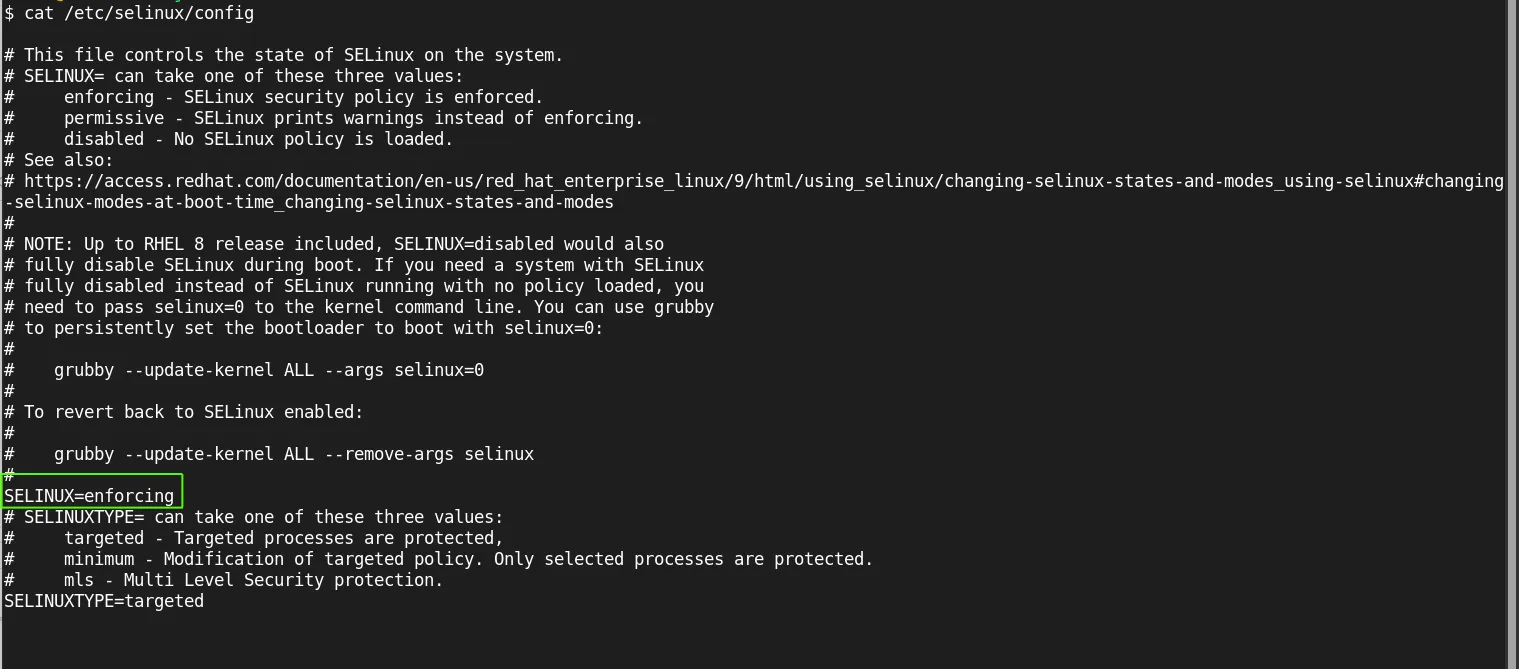
Photo by admingeek from Infotechys
Modify the following line:
SELINUX=enforcing # Change to permissive or disabled if required
Restart the system for changes to take effect:
sudo systemctl reboot
SELinux contexts define access control settings for files, directories, and processes. A context consists of four attributes:
|
|
|
|
Check file context using:
ls -Z /var/www/html/
Example output:
drwxr-xr-x. root root system_u:object_r:httpd_sys_content_t:s0 /var/www/html
Changing File Contexts |
To modify SELinux contexts, use chcon:
sudo chcon -t httpd_sys_content_t /var/www/html/index.html
However, chcon changes are temporary. To persist changes, use semanage:
sudo semanage fcontext -a -t httpd_sys_content_t "/var/www/html(/.*)?"
sudo restorecon -Rv /var/www/html
Restoring Default Contexts |
If files have incorrect SELinux labels, restore them:
sudo restorecon -Rv /var/www/html
Allowing Services via SELinux |
To permit services to access certain files, modify Booleans:
sudo getsebool -a | grep httpd
sudo setsebool -P httpd_can_network_connect on
SELinux Troubleshooting |
When SELinux denies access, check logs for violations:
sudo journalctl -xe | grep AVC
Or use sealert:
sudo sealert -a /var/log/audit/audit.log
SELinux Context Table |
| Attribute | Description |
|---|---|
| User | SELinux user identity (e.g., system_u) |
| Role | Defines the role-based access control |
| Type | Specifies the security type (e.g., httpd_sys_content_t) |
| Level | MLS level (optional) |
SELinux contexts are fundamental in enforcing security policies on RHEL 9 and CentOS 9. By understanding and managing SELinux contexts, you can enhance system security and prevent unauthorized access. Properly configured SELinux policies can significantly reduce attack surfaces by restricting unauthorized interactions between processes and files. Regular monitoring and auditing of SELinux logs can help identify and mitigate potential security breaches before they become critical.
While SELinux may seem complex initially, mastering its concepts will strengthen the overall security posture of your Linux environment. With the right configurations and practices, you can leverage SELinux to create a robust and secure system that minimizes security vulnerabilities.
Did you find this article helpful? Your feedback is invaluable to us! Feel free to share this post with those who may benefit, and let us know your thoughts in the comments section below.

Discover the best practices for securing SSH connections on Linux servers. Learn essential security tips like disabling root login, using SSH keys, and more for

Learn how to install Cluster SSH on Linux distributions of various flavors including Ubuntu, Debian, CentOS, and Fedora. This comprehensive guide will help system administrators

Learn about hardening OpenVPN security on RHEL 9 and CentOS 9 with best practices for authentication, encryption, firewall rules, logging, and intrusion detection. Table of Contents Introduction
