Resize a PNG Image Using Python

In this article, we will examine how to resize a PNG image using Python, a versatile programming language renowned for its simplicity and power, along with the Pillow library, an essential tool for image processing tasks in Python. Table of Contents Introduction In today’s digital landscape, images are an integral part of various applications, ranging […]
Install WebSphere on RHEL9 or CentOS9

In this article, we will review how to install WebSphere on RHEL9. It will include step-by-step instructions, prerequisites to ensure a smooth installation process, and insights into configuring WebSphere for optimal performance on Red Hat Enterprise Linux 9. Table of Contents Introduction WebSphere, developed by IBM, is a robust and widely used application server that […]
The distinctions between GPT1 and GPT4

Ever pondered the distinctions between GPT1 and GPT4? This article delves into the evolution of Generative Pre-trained Transformers, from its initial iteration to the cutting-edge advancements of today, aiming to shed light on the journey of progress within the GPT series. Table of Contents Introduction In the realm of artificial intelligence and natural language processing, […]
12 Leading Black Innovators in Technology | Black History Month

As we celebrate Black History Month, it’s essential to recognize the profound impact of Black innovators in technology. From pioneering groundbreaking inventions to shaping the digital landscape we know today, these individuals have left an indelible mark on the industry. Table of Contents Introduction As Black History Month unfolds, we’re reminded of the extraordinary contributions made […]
Add a Virtual Bridge Using NMCLI
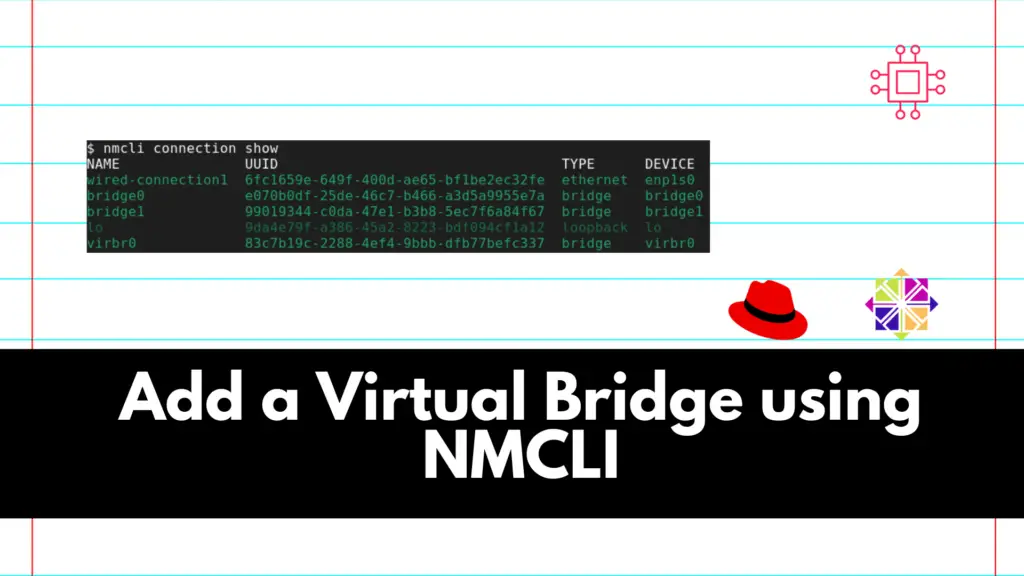
Adding a virtual bridge using nmcli involves several steps. A virtual bridge is commonly used in networking to connect multiple virtual or physical network interfaces. Table of Contents Introduction In networking, a virtual bridge serves as a crucial component for connecting and managing multiple network interfaces. It allows for the creation of a unified network […]
Calculate Trading Days in a Year Using Python

Discover how to calculate trading days in a year using Python on Linux. Understand why trading days vary annually, see 2024’s breakdown, and learn how investors use this insight to plan smarter financial strategies. Table of Contents 🔈Introduction In the dynamic world of finance, understanding the intricacies of the stock market is crucial for both […]
How to calculate pi using a bash script
To calculate pi using a Bash script, you can use the bc command, which is a tool that can perform arithmetic operations in the terminal. Table of Contents Introduction By following our step-by-step guide, you’ll learn how to calculate pi using a Bash script while gaining a thorough understanding of the underlying code. We’ll review […]
RHCSA 9 Exam Prep: Master 10 Essential Shell Scripts for Automating Linux Tasks

Are you preparing for the RHCSA 9 exam and want to master the essential skill of shell scripting? Discover 10 practical shell scripts that can automate tasks in Linux and help you excel in the exam. From conditional code execution to processing script inputs and outputs, these scripts cover all the key areas and will […]
Secure SSH with Ansible

Learn how to secure SSH with Ansible and protect your Linux systems from unauthorized access with this step-by-step guide. Table of Contents Introduction Ansible is a popular automation tool that is used for managing IT infrastructure. It was developed by Michael DeHaan in 2012 and has since then become one of the most popular automation […]
Build your own Mortgage Calculator using Shortcodes

Do you want to build your own mortgage calculator with just a few lines of code? Learn how to use shortcodes to create a custom mortgage calculator on your website! Table of Contents Introduction If you are a website owner looking to add a mortgage calculator to your WordPress site, you’re in luck. With the […]
